
A question that is often asked by operations people is “How do I securely access my EC2 instances”. The simple answer is to login into your AWS console and find the instance (server) and connect to it from the console… But that answer really does’nt answer the fundamental issue behind the question being asked. No-one wants to manually log in to the AWS console and then manually connect to their server when upgrades, maintenance or software needs installing, especially when you have many tens or hundreds of servers and services needing attention.
What is needed (and is wanted) is remote access, not just any remote access, but secure remote access.
To this end, many architectural designs feature placing Bastion Hosts (or “Jump Boxes”) into a public subnet and then remoting to the bastion host, authenticating, and “jumping” or connecting from the bastion host to the instance needing attention or maintenance (ref: diagram below)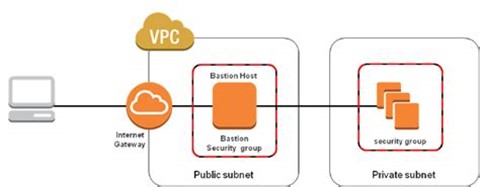
This raises the security concern of having to allow remote access (either open SSH or RDP ports) on a publicly accessible network. Implementing a combination of Network Firewall, Network Access Control List (NACL), Security Group (SG) and host Operating System firewall does add additional layers of defence, but the fundamental underlying security issue remains – namely that the packet of data from the client to the bastion host could be “sniffed”, analysed, and used by an attacker to gain access.
A more secure solution would be to replace the standard Bastion Host with a VPN Server/Bastion. This would ensure that all internet traffic between the client and VPN bastion is encrypted end to end (from the client PC to bastion). Problem solved! However… this raises another operational issue – the fact that each client PC will need the associated VPN software installed and configured and will add both additional load (in the form of CPU use) and additional network latency.
AWS offers a service which fulfils the requirements of secure remote access and much more in one bundle. AWS Systems Manager is a collection of capabilities to help you manage your applications and infrastructure running in the AWS Cloud (and, if required, on premises). Systems Manager simplifies application and resource management, shortens the time to detect and resolve operational problems, and helps you manage your AWS resources securely at scale.
A general example of Systems Manager process flow
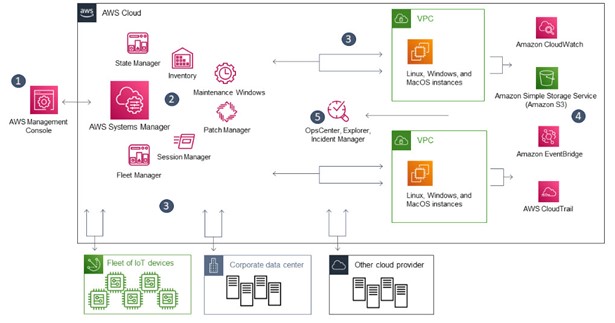
- Access Systems Manager – There are several available options for accessing Systems Manager, including the Graphic User Interface (GUI) of the AWS console, Command Line (CLi) or Software Development Kit (SDK).
- Choose a Systems Manager capability – Determine which capability can help you perform the action you want to perform on your resources. The diagram shows only a few of the capabilities that IT administrators and DevOps personnel use to manage their applications and resources.
- Verification and processing – Systems Manager verifies that your AWS Identity and Access Management (IAM) user, group, or role has permission to perform the action you specified. If the target of your action is a managed node, the Systems Manager Agent (SSM Agent) running on the node performs the action. For other types of resources, Systems Manager performs the specified action or communicates with other AWS services to perform the action on behalf of Systems Manager.
- Reporting – Systems Manager, SSM Agent, and other AWS services that performed an action on behalf of Systems Manager report status. Systems Manager can send status details to other AWS services (if configured).
- Systems Manager operations management capabilities – (if enabled) Systems Manager operations management capabilities such as Explorer, OpsCenter, and Incident Manager aggregate operations data or create artifacts in response to events or errors with your resources. These artifacts include operational work items (OpsItems) and incidents. Systems Manager operations management capabilities provide operational insight into your applications and resources and automated remediation solutions to help troubleshoot problems.
By integrating Systems Manager with AWS Key Management Server (KMS) you can specify that session data transmitted between your managed nodes (instances and/or physical servers on premises) and the local machines of users in your AWS account is encrypted using KMS key encryption. (This is in addition to the TLS 1.2 encryption that AWS already provides by default.) AWS KMS encryption is available for Standard_Stream, InteractiveCommands, and NonInteractiveCommands session types.
If you’d like to know more, join me on one of our System Operations on AWS courses where you can configure Systems Manager yourself, or ask for a quick demonstration to see how I can securely remote into a Linux instance (bash shell) from my PC Windows command prompt …




